Endgame Gear Malware Incident: A Wake-Up Call for Supply Chain Security Gaming peripheral company Endgame Gear recently confirmed a serious security breach involving their mouse configuration software. A trojanized version of the tool was discovered on their official website, potentially exposing…
The trailer for Avatar: Fire and Ash is finally here and teases Pandora’s most terrifying adversary yet
Avatar: Fire and Ash Trailer Ignites Marketing and Branding Inferno – What Businesses Can Learn The trailer for Avatar: Fire and Ash has dropped, offering a glimpse into Pandora’s newest threat and a fiery masterclass in marketing and branding. But beyond…
Meta revealed what makes a VR game perfect, and it could be hinting at big hardware changes
Meta’s VR Vision: What a 20-Minute Sweet Spot Means for Businesses and Governments Meta’s recent revelation that the ideal VR gaming session lasts between 20 and 40 minutes offers more than just a glimpse into gamer behavior. It’s a strategic signal…
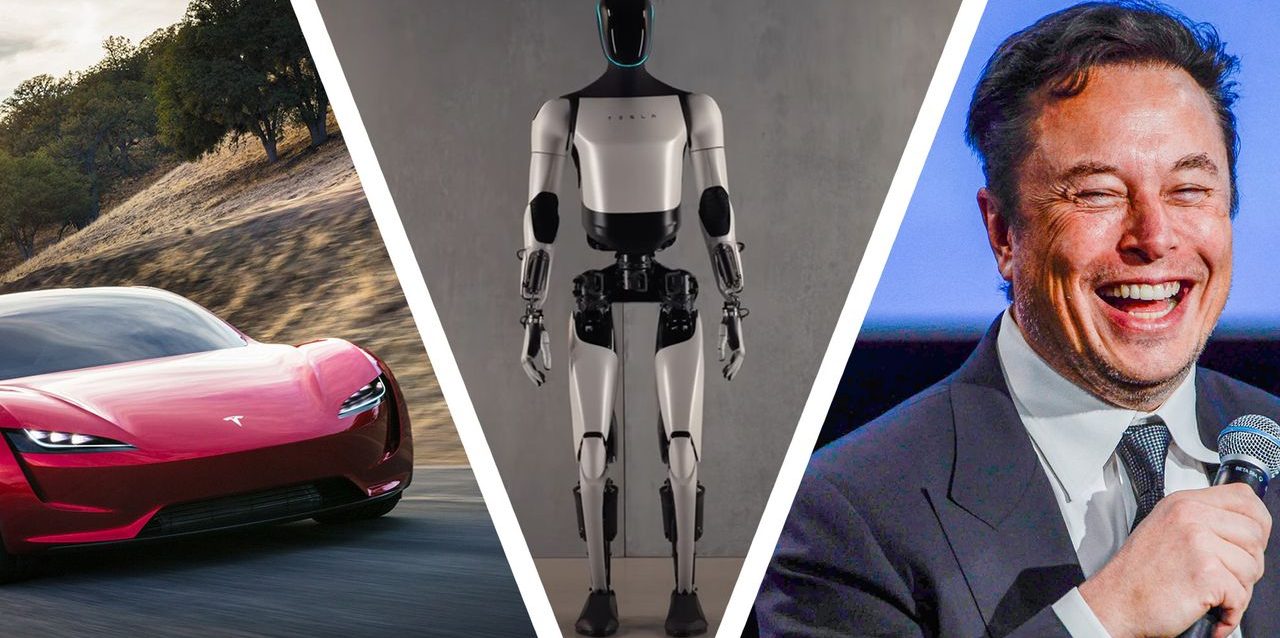
Tesla just signed a $16.5 billion contract with Samsung to manufacture an AI chip used in humanoid robots, data centers and, oh yes, autonomous cars as well
Tesla’s $16.5 Billion Bet on AI: A Game-Changer for Businesses and Governments Tesla’s recent $16.5 billion contract with Samsung to produce its AI6 chip signifies a major leap forward in the development and deployment of artificial intelligence, with far-reaching implications across…
The Google Home crisis deepens as users report full meltdown – and a lawsuit could be on the way
Google Home Meltdown: What Businesses and Governments Need to Know The ongoing issues with Google Home devices, escalating from user reports of malfunctions to the potential for legal action, represent a crucial lesson for organizations of all sizes about the risks…
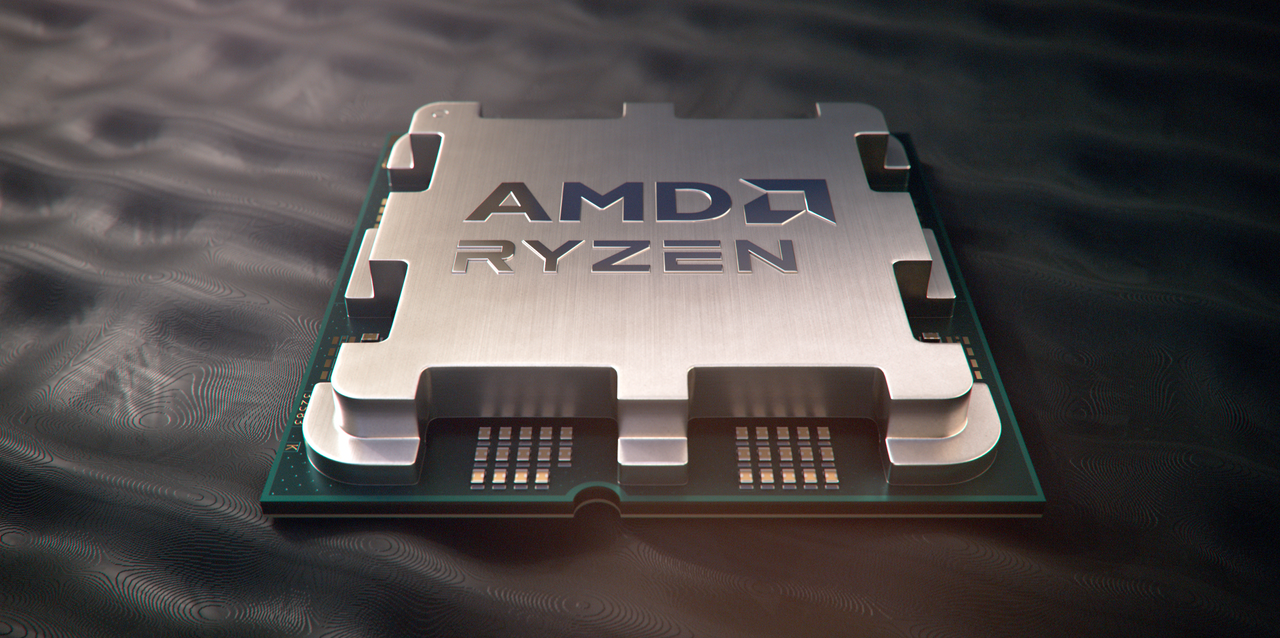
AMD CEO says its chips made in the US will be up to 20% more expensive, but claims that it’ll be worth the price hike
Made in the USA: AMD’s Strategic Shift and the Implications for Businesses and Government AMD CEO Lisa Su’s statement about potential price increases for US-made chips has sent ripples through the tech industry. While a potential 20% price hike might seem…
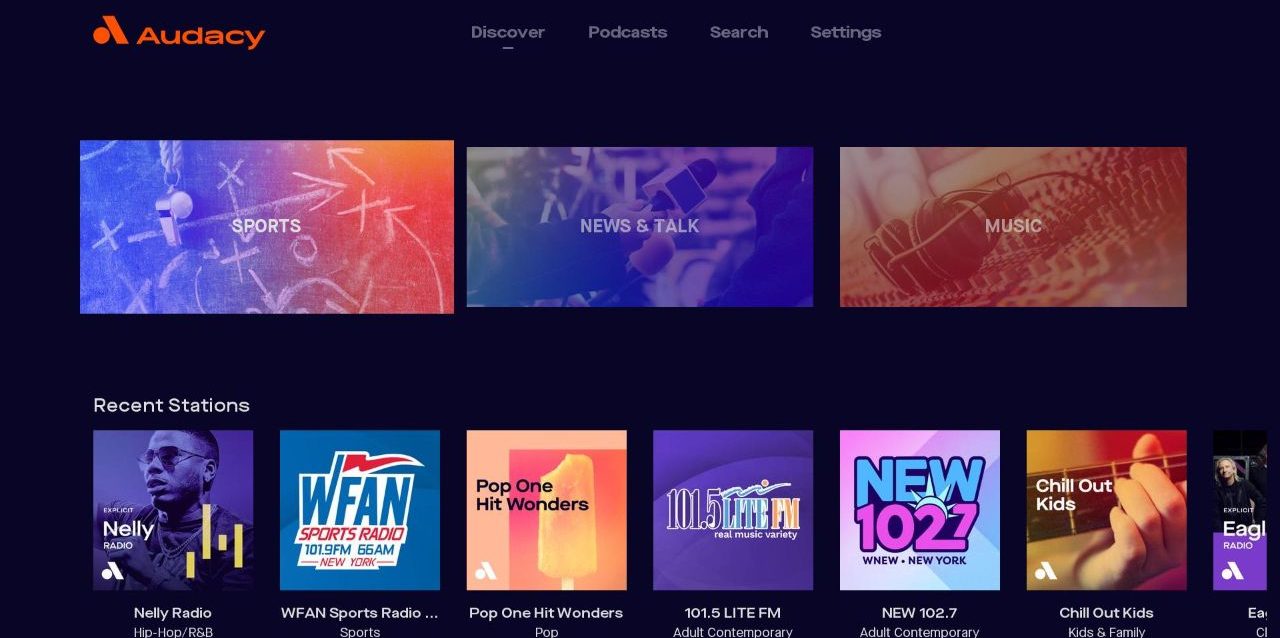
Roku just lost popular music streaming app Audacy – here are the best alternatives
Roku Users Lose Audacy: Navigating the Streaming Landscape and Exploring Alternatives Roku users recently discovered the Audacy music streaming app is no longer available on the platform. While the specific reasons behind this removal remain unclear, this development highlights the dynamic…
BuzzSprout Review
Beyond Buzz: Why Podcast Hosting Matters for Your Brand Choosing the right podcast hosting platform is crucial for any organization looking to leverage the power of audio. While the original article highlighted BuzzSprout for its user-friendliness, speed, and support, it’s important…
ByteDance AI tool Trae caught spying on users
ByteDance’s Trae AI Tool Raises Privacy Concerns: What Businesses and Governments Need to Know ByteDance, the company behind TikTok, is facing scrutiny over its Trae AI tool. Reports indicate that Trae collects substantial user, project, and system data, even when users…
There’s one way Apple could make Macs true gaming machines, and it’s not a better chip
Unlocking the Mac’s Gaming Potential: It’s Not About the Chip Apple’s foray into the gaming market faces a surprising hurdle: the Magic Mouse. While the company’s silicon advancements have significantly boosted the Mac’s processing power, the mouse itself remains a major…